Welcome › Forums › Appliance and OS › Cost & Savings via Precinct
- This topic is empty.
- AuthorPosts
- June 30, 2023 at 2:05 pm #3487
Mike Riforgiate
KeymasterCost and Savings Report
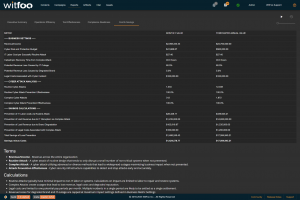
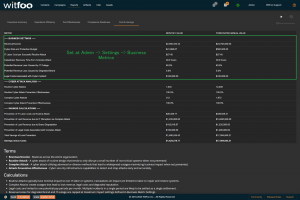
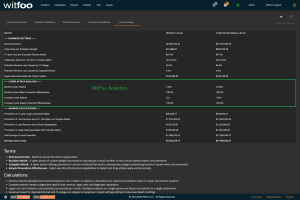
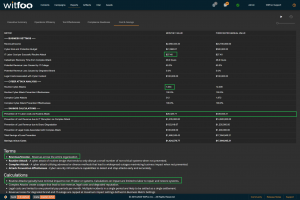
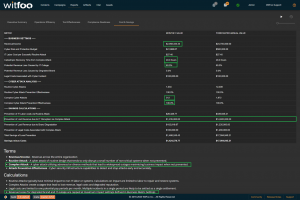
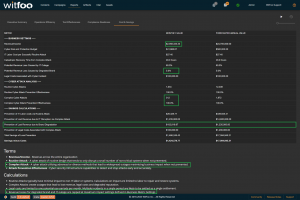
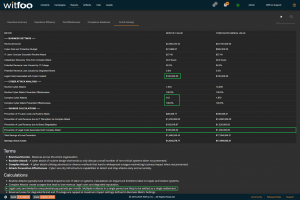
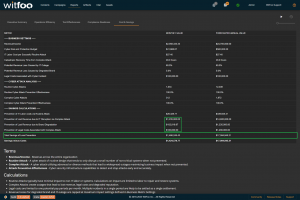
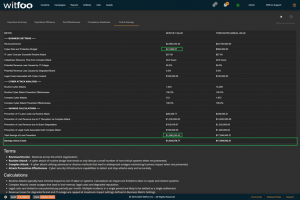
Precinct 6.3 introduces the Cost and Savings report. The report autonomously calculates the effectiveness of the cybersecurity budget in accounting terms.
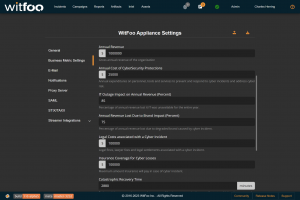
The first section of the report defines the metrics unique to the organization. The metrics include revenue, the total cybersecurity budget, labor costs, restoration times and cybersecurity impacts to revenue.
These settings can be configured under Admin > Settings > Business Metric Settings.
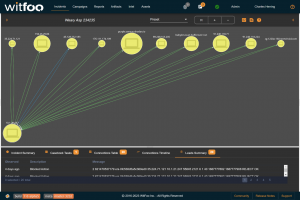
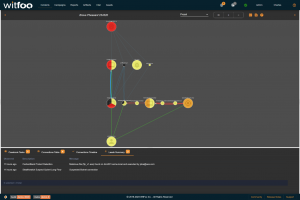
The second section of the report is autonomously calculated. WitFoo Precinct receives messages from all devices, security tools, IT systems and data lakes. This data is analyzed to create units of work that map to specific types of cyber incidents including extortion via ransomware, trespassing via phishing, data theft, financial fraud.
Most attempted cyber incidents use simple tactics that are routinely stopped. WitFoo Precinct categorizes these units of work as routine attacks. The potential damage of these attacks are generally limited to IT labor for restoration and repair of a limited set of systems.
Complex attacks combine multiple tactics or advanced techniques. They are more focused and have the potential of causing lasting damage to a business. Successful complex attacks will cause IT Outages, degrade the victim’s brand and may prompt legal fines and settlements.
“Prevention of IT Labor Costs via Routine Attacks” is calculated by multiplying the units of work for Routine Cyber Attacks, against successful prevention and IT Labor Costs. This number represents the cost to the business in utilizing internal or external labor to restore systems if the security investments did not stop the routine attacks. Note that this cost can be larger than revenue because it is bound to required labor and is not connected to revenue.
“Prevention of Lost Revenue due to IT Disruption” calculates the negative impact to revenue if the observed complex attacks were not stopped by the security infrastructure. It is calculated by first establishing IT Outage time. This is accomplished by multiplying “Catastrophic Recovery Time” by the number of stopped units of work associated with complex attacks. If the amount of clock time exceeds the available time in the period, the maximum time in the period is used. The “outage time” is multiple against revenue and “Potential Revenue Loss Caused by IT Outage.”
“Prevention of Lost Revenue due to Brand Degradation” is calculated by multiplying “Potential Revenue Loss Caused by Degraded Brand” by Revenue when at a complex attack is detected. Multiple successful complex attacks will only result in a single loss against brand degradation.
“Prevention of Legal Costs Associated with Complex Attack” is calculated “Legal Costs Associated with Cyber Incident” when a complex attack is detected and stopped. Multiple successful attacks in a period will typically only lead to a single set of legal costs.
“Total Savings of Loss Prevention” is calculated by summing the preceding 4 calculations. It represents the total savings of costs and lost revenue delivered by the security investments.
“Savings minus Costs” is the “bottom-line” of Cyber Security and is calculated by subtracting the Budget from the Savings.
- AuthorPosts
- You must be logged in to reply to this topic.